I can’t believe it.
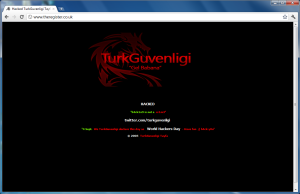
I would never have thought that one of my favourite tech news sites could ever be hacked. Yet a few minutes ago I captured the following screenshot when browsing.
Come on guys, what is going on?
*Updated – 10:00pm 4th September 2011
After further investigation, it seems that The Register’s website was not hacked as such, but rather the DNS for that domain has been hijacked.
The bad A record IP appears to be 68.68.20.116 instead of 212.100.234.54 which is a rackspace server where the register is hosted.
If you go to all-nettools.com and do a nameserver lookup you’ll see the register has the following nameservers now:
theregister.co.uk. 86129 IN NS ns4.yumurtakabugu.com.
theregister.co.uk. 86129 IN NS ns2.yumurtakabugu.com.
theregister.co.uk. 86129 IN NS ns1.yumurtakabugu.com.
theregister.co.uk. 86129 IN NS ns3.yumurtakabugu.com.
Which isn’t right.
It should probably look something like:
theregister.co.uk nameserver = ns1.theregister.co.uk
theregister.co.uk nameserver = ns2.theregister.co.uk
theregister.co.uk nameserver = ns3.theregister.co.uk
theregister.co.uk nameserver = ns4.theregister.co.uk
theregister.co.uk nameserver = ns5.theregister.co.uk
theregister.co.uk nameserver = ns6.theregister.co.uk
*Updated – 11:00pm 4th September 2011
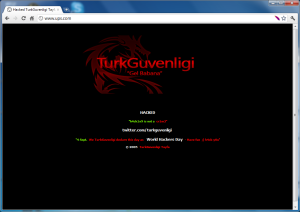
It appears that ups.com has also been hacked.
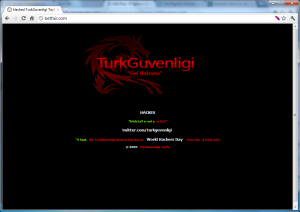
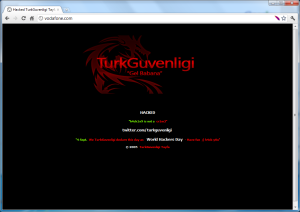
*update again… Sites that have also been defaced include
betfair.com
acer.com
vodafone.com
telegraph.co.uk
http://www.zone-h.org/archive/notifier=TurkguvenLigi.info
*Updated – 7:15am 5th September 2011
The Guardian have interviewed the Turkish hackers that instigated the attack on the various high-profile websites. http://www.guardian.co.uk/technology/2011/sep/05/dns-hackers-telegraph-interview
*Updated – 8:10am 5th September 2011
The Register have now posted an article explaining a little about what happened.
http://www.theregister.co.uk/2011/09/05/dns_hijack_service_updated/
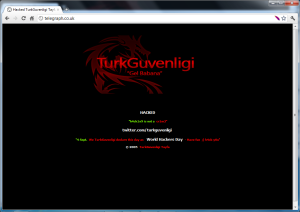
Omg that whas my favourite website, why would someone do that.
I hope they get it all sorted out
DNS poses the biggest security risk to any organization
Just seen that as well! Will be interesting to read the editorial on Monday 🙂
Shaun
Yep, noticed same thing, figured it was some joke… Seems not….
Question is how….
Thinks its only very recently happened also….
Looks like a jackass randomly targeting any old Web sites he can manage to compromise, for no other purpose than to get notoriety for himself. He took a kitchen-sink approach and these are the ones that went down the drain. There’s no obvious ethical or political agenda at work in breaching those wildly different sites.
I doubt the website it self was hacked, looks like some trickery with the DNS servers meaning you are actually being sent to a completely different website. Worst part is if they wanted to, they could just make their “fake” site look like the real thing, and steal user passwords and such without people ever knowing.
…he stole my logo for my website, I paid to have that designed several years ago.. I hate hackers
Appears to be a registration attack. According to Netcraft the site moved to BlueMile today, September 4, 2011. Other sites hosted there are mostly porn.
Netblock Owner IP address OS Web Server Last changed
Bluemile, Inc 226 N. 5th St Suite 300 Columbus OH US 43215 68.68.20.116 Linux Apache/2.2.17 Unix mod_ssl/2.2.17 OpenSSL/0.9.8e-fips-rhel5 mod_auth_passthrough/2.1 mod_bwlimited/1.4 FrontPage/5.0.2.2635 mod_perl/2.0.4 Perl/v5.8.8 4-Sep-2011
http://toolbar.netcraft.com/site_report?url=http://theregister.co.uk
All these sites work fine for me, from Ireland.
Is it more likely your ISP has had their recursive nameservers hacked? Or maybe a root server close to you?
dig trace NS theregister.com is giving the correct results from Irish and UK servers.
On top of this El Reg was running a version of Apache (2.2.16) vulnerable to CVE-2011-3192 which leaves it open to an effective DoS.
I fired off an e-mail to ipadmin@bluemilenetworks.com, who supposedly administrates the IP address block which contains the one that is being used to host the dummy site. Guess we will see if they can do anything, now.
theregister.co.uk. 600 IN A 72.3.246.59
theregister.co.uk. 600 IN NS ns1.theregister.co.uk.
It loos fine from here. Perhaps the DNS problem is on your end?
I am not the only one that has seen the issue.
Right. Perhaps the others are using the same cache-poisoned or compromised nameserver as you. But I assure you, theregister.co.uk is resolving fine and the website is up.
You sure your nameserver/ISP/whatever, or even your computer, is hacked instead?
I am not the only one that has seen the issue. Many others from various different ISP’s.
Fact is they all have the same registrar, which is ASCIO (http://www.ascio.com).
Most likely it that was compromised, which would explain how the nameservers got changed… just my 2 cents…
I can’t even reach theregister. Site won’t load.
My own recursing named nameserver resolves fine.
dig theregister.co.uk. any @8.8.8.8 # this works fine too. But:
dig theregister.co.uk. any @4.2.2.2 # ouch!
…
theregister.co.uk. 37457 IN NS ns2.yumurtakabugu.com.
theregister.co.uk. 37457 IN NS ns1.yumurtakabugu.com.
theregister.co.uk. 1631 IN A 68.68.20.116
4.2.2.2 is not actually a public nameserver, but it has been left open for a long time. Are you using it? If so, stop.
So, it seems more like it’s a REGISTRAR that’s been hacked — not The Register.
Domain name attacks like this can be done via social engineering, such as password recovery or actually tricking somebody at the DNS registrar to disclosing info. This has been around forever, albeit not a full system compromise but ugly as it takes a long time to clear up.
Turkish hackers target theregister.co.uk perhaps political motive behind it. Site is now down.
simply wordpressed
“Gel Babana” translates to “Come to your daddy”
Guardian link is broken – you’ve got too many mentions of http at the start of the url.
Thanks. I have now fixed that.
http://www.theregister.co.uk/2011/09/05/dns_hijack_service_updated/
So this was real, and as others have said, it was a compromise at the registrar, not at The Register. The probable reason why I did not see it: the co.uk parent domain changes had been reversed before I checked.
This incident is a good example of why I recommend NOT using one’s ISP nameservers. The benefit of cache hits being slightly faster is offset by the TTL being, on average, half of what you would get by doing your own recursion to the authoritative NS. And then you get to share in the cache poisoning with all the other users.
Yes, my recursive resolver could get a poisoned cache as well, but the window of opportunity for mischief is much smaller. And I can flush the cache if I suspect something is amiss.